5 Best Open Source Software For Enterprise Network Security
Open-source software is free and flexible to configuration
- The advantage of open-source network security software is that it's free and flexible for any customization.
- Some of the tools provide network identification and threat detection while others help you fight back the threats.
- However, because there is no commercial guarantee, you will need a powerful IT team to configure all their features.
Open-source software is the core concept for development because it is free to modify and adapt to your needs. And nothing is more configurable than network security software. Here, you will find the best open-source tools for enterprise network security.
Why would I choose open-source software?
Cybersecurity tools protect enterprises from all threats and open-source software is a low-budget, flexible solution for that.
However, you will need to have a strong team with high technical expertise to configure and implement the solution.
We have chosen the tools below based on their features and readiness in terms of network security and integrations.
What are the best open-source network security tools?
Wazuh – Best network privacy security
If you’re looking for the best open-source network security tool, the answer is Wazuh.
Of course, it’s an open-source solution that ensures protection for workloads across on-premises, virtualized, and cloud-based environments.
In other words, it’s an enterprise-level tool for both Cloud and endpoint security. Its agents for Windows, Linux macOS, Solaris, AIX, and HP-UX systems are capable of detecting any anomaly or rule-based transgression.
And it does that by scanning all the network components and their logs, to provide information for the central manager that will analyze and store it.
As a change in file content, attributes and permissions are viewed as privacy threats, Wazuh constantly monitors any such modifications.
However, it doesn’t just alert you, it’s also able to block access to the affected system or execute commands to remedy the situation.
Another strong advantage for Wazuh is the list of integrations with other services and tools such as YARA, AlienVault, Amazon Macie, VirusTotal, and many more.
The solution is free so that you can implement it immediately but if you need technical assistance, you will have to pay a fee.
Let’s review some of its key features:
- Analyzes data received from the Windows, Linux macOS, Solaris, AIX, and HP-UX systems agents and processes it using threat intelligence
- Review regulatory compliance, vulnerabilities, file integrity, configuration assessment, and not only Cloud security but Container security as well (for Docker hosts and Kubernetes notes and down to the container level itself)
- Web user interface for data visualization, analysis, and management
- Advanced threat intelligence features
- Malware detection and log data analysis

Wazuh
Protect your network environment with a complete XDR and SIEM network cybersecurity solution.AlienVault OSSIM – Great SIEM solution
The OSSIM acronym from AlienVault OSSIM stands for Open Source Security Information and Event Management.
Compared to Wazuh, which also has XDR components to fight off the attacks, this solution only has SIEM features.
That means, it can detect network events and alert you so you can make the necessary changes to resolve the possible issue.
In short, AlienVault OSSIM offers asset discovery, vulnerability assessment, intrusion detection, behavioral monitoring, and SIEM event correlation.
The software is based on the proprietary Open Threat Exchange (OTX) that involves users contributing and receiving real-time information about malicious hosts.
Here are some of its most important features:
- Monitors on-premises physical and virtual environments
- Asset discovery and inventory
- Extensive vulnerability assessment
- Powered by Open Threat Exchange (OTX)
- Community support via product forums
OpenEDR – Ideal for endpoint malware protection
OpenEDR is a free, open-source endpoint detection and response software. It provides real-time analytic detection with Mitre ATT&CK visibility.
It basically offers event correlation and root cause analysis of malicious threat activity and behaviors to help you protect your network.
One of the best advantages of OpenEDR is that it can be deployed on any endpoint environment and has a cloud-based management console.
And if you want to build integrations for it, it’s as simple as using its GitHub source code.
Let’s review some of its key features:
- Enable continuous and comprehensive endpoint monitoring
- Correlate and visualize endpoint security data
- Perform malware analysis, anomalous behavior tracking, and in-depth attack investigations
- Enact remediations and harden security postures to reduce risk on endpoints
- Stop attempted attacks, lateral movement, and breaches
Metasploit – Great for network penetration testing
If you have a strong IT management team, Metasploit can be an excellent tool to test your network vulnerability.
The software can be used to run security assessments, anticipate attacks and improve overall cybersecurity awareness.
A great advantage is that it is very flexible. You can install it on Windows (64-bit), macOS, and Linux workstations.
Moreover, you will find ready-to-use installers for fast implementation. And then, Metasploit can automate almost all the phases of a penetration test, starting with exploit tactics and ending by collecting evidence.
Here are some of its best features:
- Extensive penetration tests
- Works on Windows, macOS, and Linux systems
- Great implementation flexibility
- Easy to deploy and use
Nmap – Good for network scanning
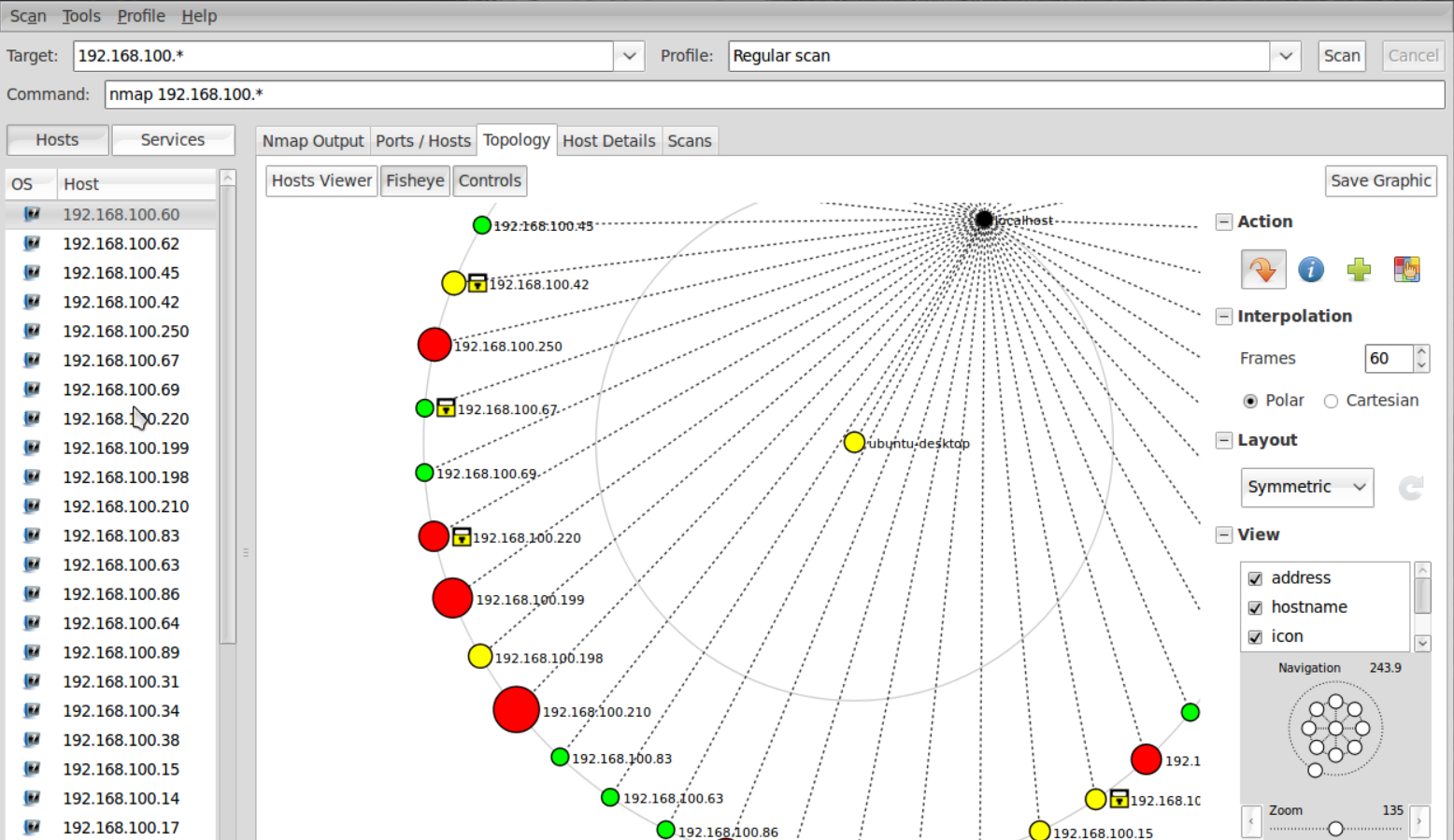
Besides appearing in Matrix Reloaded and Ocean’s 8 as a hacking tool, Nmap is actually a network mapping and visualization tool.
Network administrators can use it also for network inventory, managing service upgrade schedules, and monitoring host or service uptime.
Nmap uses raw IP packets to identify which hosts are available on the network, what services are offering, what OSes they are running, and a lot more.
The tools can scan large networks very fast, and runs on all major computer operating systems. You will find official binary packages for Linux, Windows, and Mac OS X.
It comes as a command line terminal but you may also install an advanced GUI and results viewer called Zenmap.
There are also other integrations available such as Ncat (a flexible data transfer, redirection, and debugging tool), Ndiff (for comparing scan results), and Nping (a packet generation and response analysis tool.
Check out its key features below:
- Supports dozens of advanced techniques for mapping out networks filled with IP filters, firewalls, routers, and other obstacles
- Scans huge networks of literally hundreds of thousands of machines
- Most operating systems are supported, including Linux, Microsoft Windows, FreeBSD, OpenBSD, Solaris, IRIX, Mac OS X, HP-UX, NetBSD, Sun OS, Amiga, and more
⇒ Get Nmap
This concludes our selection of the best open-source network security software for your enterprise.
We hope that our article helped you select the right tool for your needs and that now you have broadened your choices.
You might also be interested to check our list of the best open-source antiviruses for your system.
If you have any other suggestions of software that fits this category, let us know about them in the comments section below.