Teams is prone to modern malware, new research shows
The vulnerability allows the bypassing of security controls.
- The vulnerability exists in the latest version of Microsoft Teams.
- Hackers can bypass security controls using IDOR.
- However, the hacker must buy a similar domain and register it with M365.

Recently, a study has shown that over 80% of Microsoft Teams accounts were hacked at least one time, in 2022. What’s even more worrying is the fact that the same study reported that 60% of Microsoft Teams accounts were successfully hacked. That is a worrying number, but just how easily can Microsoft Teams be hacked, in this case?
Well, it turns out Teams can be very easily hacked. New research conducted by JUMPSEC’s Red Team discovered that Team is actually prone to modern malware. And external tenants can easily bring malware into Microsoft Teams as well.
How can this happen? There is a vulnerability in the latest version of Microsoft Teams. This vulnerability allows the malware to infiltrate any organization using Microsoft Teams in its default configuration.
The hacker can bypass the client-side security controls. These security controls prevent external tenants from sending files (malware in this case) to staff in your organization.
IDOR in Microsoft Teams allows for the introduction of malware
The exploitation is possible through a vulnerability in the client-side security controls. In Microsoft Teams, certain security controls can be implemented client-side.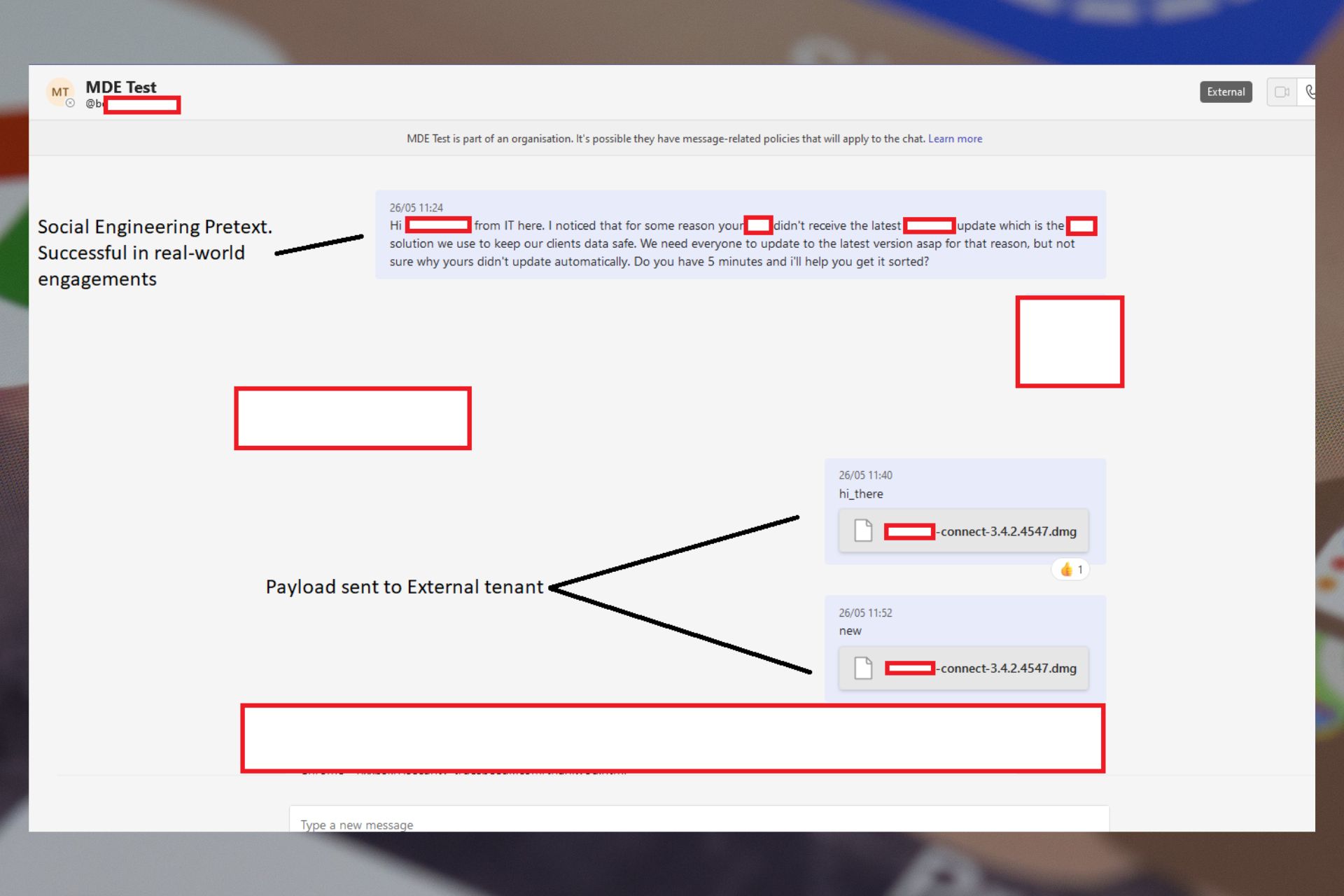
So that means one hacker can impersonate an individual from your organization, and by bypassing these controls, they will be able to send you malicious files. This coupled with another vulnerability, allows the hacker to send malicious files directly into your inbox.
The research states that this method can bypass nearly all modern anti-phishing security controls. However, it requires the hacker to buy a domain similar to your target organizations and register it with M365.
But it impacts every organization using Teams in the default configuration, so this vulnerability has a huge potential for being exploited by threat actors.
The vulnerability was acknowledged by Microsoft, and the Redmond-based tech giant even validated its legitimacy. However, the tech giant said it did not meet the bar for immediate servicing.
There are still things your organization can do to protect themselves. According to the research, you can do the following:
- Review if there is a business requirement for external tenants to have permission to message your staff.
- Educate staff on the possibility of productivity apps such as Teams, Slack, Sharepoint, etc, for launching social engineering campaigns.
As you can see, while Teams is a very popular app for organizations to use, it’s also extremely vulnerable to attacks. However, since vulnerabilities like these are often patched in updates, you should also keep your Teams updated to the latest version, all the time. You can read the research in full here.
What do you think about this vulnerability? Be sure to let us know in the comments section below.